As technology has advanced, hackers are now commonly referred to as cybercriminals due to the sophistication of their actions.
Have you ever wondered what would happen if a hacker entered your phone or laptop and stole your important information?

But do not panic when ethical hacker Laura Kankaala, a "White Hat," who was trained in ethics, reveals signs your phone has been compromised by the hacker.
Featured on a TV series, Kankaala demonstrates a simple hack, transitioning from a smart home device to a compromised car.
Kankaala issues a warning when a dot appears on the screen of your phone.
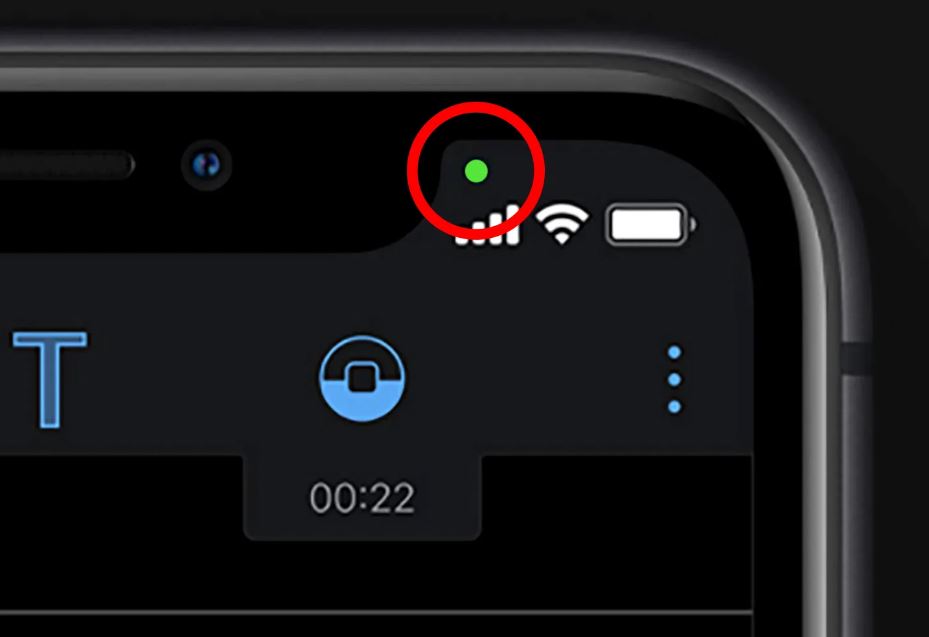
According to Kankaala, if you spot a green dot on the Android screen or an orange dot on the iPhone, your advice may be compromised. This means that a hacker or someone else has installed a suspicious application on your phone.
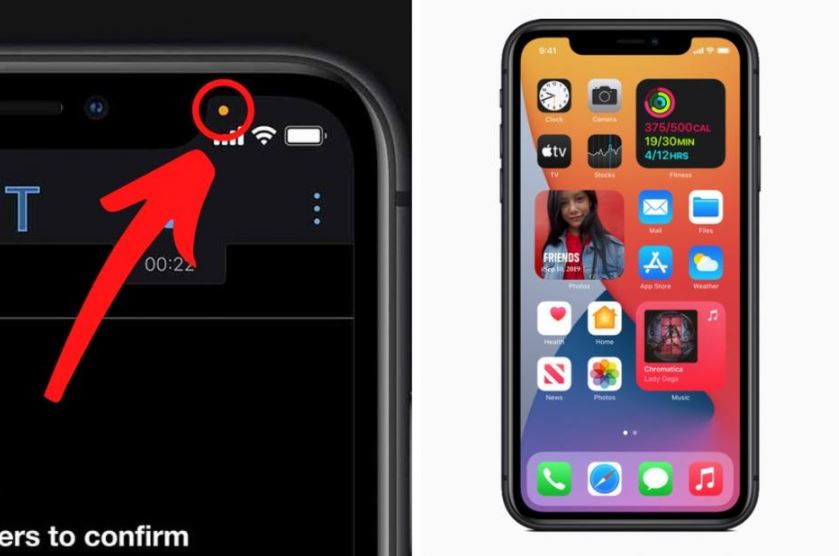
Furthermore, Kankaala said that the dot on your screen not only signifies the activation of the device's microphone or camera but also indicates that your phone is running malicious software.
She explained that these warning dots signal the activation of the device's microphone or camera, serving as an alert that the phone may be running malicious software designed for unauthorized surveillance.
She added, ‘As an ethical hacker, you would know someone is inside your phone because I would tell you and help you remove my access'.
Kankaala warned that malware may record audio or read messages by using your microphone and tracking your location.
She continued: ‘Cyber criminals can employ malware like this or even an abusive person you know in the form of stalkerware.’
So, Kankaala advises that you should review your installed apps and remove any unfamiliar ones. Additionally, you can run a virus scan application.
On an iPhone, you can check which of your apps utilize the camera or mic by going into the phone's Control Center and reviewing the dots icon at the top.
This should reveal which apps are using your microphone, camera, or location.
Your phone begins to heat up.
According to Kankalaa, the warming up of a phone may indicate the presence of malicious software or that your phone will share a continued location.

Additionally, you might spot strange-looking apps that you either do not recall downloading to your phone or that you may have inadvertently downloaded from somewhere other than the official app store.
If you get emails from social media apps, your phone may be compromised.
One day, you may accidentally receive an email from your bank or social media platform asking if you want to change your password.
Be cautious; this could be a sign that your phone has been compromised or that your information has been stolen.
Kankaala explained that hackers often use phishing attacks to accomplish this, targeting victims through calls and texts.

She explained: 'It's very easy to impersonate phone numbers of financial institutions or other well-known parties and attempt to manipulate you to do something that's against your best interest—for instance, do an instant monetary transaction or give out your credentials to online services.'
Your bank calls you: It could be a scam.
The hackers often target victims through calls and texts, and they don't necessarily need to install dodgy apps on your phone.
Even if the number appears to be correct for your bank, it might still be a scam.
Hackers frequently impersonate the phone numbers of financial institutions or other well-known entities to force victims to do something.
Kankalaa said: ‘One of the easiest ways to target people using mobile phones with different sorts of scams is via text messages and phone calls.'






